blog
RSA 2023 (Stronger Together), wrapped up in San Francisco last week. On Monday, I presented a session on cloud security and cloud identity. Then used some free time on Tuesday to attend a few sessions, learn from other cloud security experts, and join Stephen A. Hart for a live Wait Just an Infosec broadcast from the SANS booth.

Overall, here were some key takeaways from RSAC 2023:
Attackers have been breaching the cloud for years by stealing long-lived credentials. To combat these attacks, cloud providers have been building improved authentication workflows for external identity providers. This technical session explores Workload Identity Federation and how you can replace long-lived cloud credentials with short-lived tokens signed by your OpenID Connect identity provider.
Service to service authentication across multiple cloud providers has historically required customers to create long-lived cloud credentials: AWS Access Keys, Azure Service Principal Client Secrets, and Google Cloud Service Account keys. Managing long-lived credentials creates important security responsibilities for customers, such as secure secrets storage and rotation. Unfortunately, organizations are failing to follow these best practices, instead storing the credentials in version control systems, deployment packages, and environment variables. Attackers stealing long-lived cloud credentials often find themselves with over permissioned access to cloud resources and an easy path for data exfiltration.
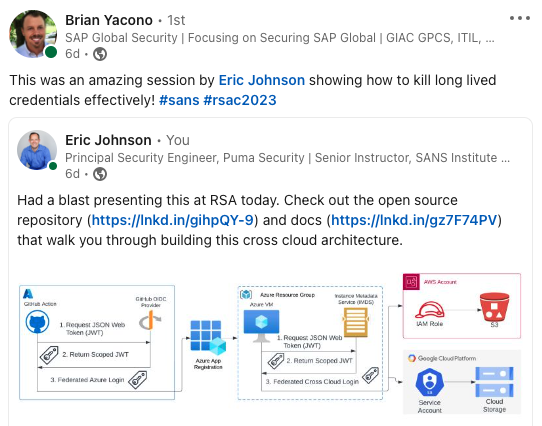
The session starts by walking attendees through a real world scenario where long-lived credentials are stolen from a cloud hosted Continuous Integration (CI) pipeline. Demonstrations show how stealing an Azure Service Principal Client Secret from a GitHub Action can allow an attacker unauthorized access to Azure resources. Attendees then learn how to configure Azure Federated Identity to trust GitHub’s identity provider and eliminate the long-lived credential.
Shifting focus back to the real world scenario, we explore an Azure virtual machine that requires access to resources hosted in both AWS and Google Cloud. Demonstrations show how a vulnerability allowing access to the Azure virtual machine’s file system can allow attackers to discover long-lived credentials and pivot into the other cloud providers. Attendees then learn how to configure trust between the Azure virtual machine’s identity and both the AWS Identity Provider and Google Cloud Workload Identity Federation resources.
The session concludes by demonstrating the functional system without a single long-lived credential. The GitHub Continuous Integration (CI) pipeline requests temporary credentials for creating the Azure virtual machine, and then the Azure virtual machine requests temporary credentials for accessing both the AWS and Google Cloud resources.
Security teams are spending too much time protecting, monitoring, and rotating long-lived cloud credentials.
Invest in efforts to configure trust between public cloud identity services (Azure, AWS, and GCP) and an OpenID Connect (OIDC) identity providers.
Slowly, over time, destroy long-lived cloud credentials to reduce your organization’s attack surface.
Session Recording - TBD

Abhay Bhargav and Anushika Vadlamudi, AppSecEngineer, presented a learning lab titled Purple Team Cloud Security Ninja early Tuesday morning. Coffee in hand, I jumped in and started solving the challenges. This learning lab provided a great experience for attendees to deploy, exploit, and harden cloud security misconfigurations in AWS, Azure, and GCP.
Chris Farris, Cloud Security Architect and fwd:cloudsec organizer, presented a session titled Walking on Broken Clouds on Tuesday afternoon. I dropped in on this session live and loved the real life lessons learned from building enterprise cloud security programs.
Anna McAbee and Sarah Currey, AWS Security, presented a session titled Top 10 Ways to Evolve Cloud Native Incident Response Maturity on Wednesday. Unfortunately, I didn’t have a chance to catch this one live due to scheduling conflicts. This one is on the top of my list to watch when the recording is available.
Would you like to learn more about Cloud Identity and Workload Identity Federation? Contact us today: sales [at] pumasecurity [dot] com.
Eric Johnson’s experience includes performing cloud security reviews, infrastructure as code automation, application security automation, web and mobile application penetration testing, secure development lifecycle consulting, and secure code review assessments.